
Securing the Future: A Deep Dive into ReactJS Security for Scalable Applications
Every modern interaction you take part in – whether it’s browsing a catalogue of products or checking your blood pressure – relies on some kind of web interface. And behind the majority of those seamless experiences is one thing: ReactJS.
But what you perceive as presenting beautifully can have crippling vulnerabilities underneath. With every dynamic component, third-party library, and API Call, the door to security vulnerabilities continues to widen just a little more.
And, this is where genuine engineering maturity is revealed.
At GKM IT, we don’t only build fast apps. We build smarter, scalable apps, and secure apps. Because ReactJS development is not about performance or design anymore, it’s about trust.
Understanding ReactJS Security Risks
Even though ReactJS has a robust architecture, React Security Risks still exist, especially when developers ignore common attack surfaces. Here are some examples of threats React developers are exposed to:
1. Cross-Site Scripting (XSS)
By default, React escapes content, but dangerous coding patterns (e.g., dangerouslySetInnerHTML) or unsafe React libraries can sometimes introduce malicious scripts.
2. Insecure State Management
When you store sensitive information like access tokens in localStorage, it can expose that data to scripts running in the browser.
3. Vulnerable Dependencies
Many third-party React libraries come with outdated packages. If these dependencies aren’t patched, they can create security vulnerabilities in React, often without developers even being aware of it.
4. Over-Exposed API Endpoints
When APIs aren’t properly secured, they can turn into easy entry points for attackers looking to mess with your React ecosystem and manipulate client-side logic.
At GKM IT, we take these threats seriously. That’s why we make it a point to incorporate threat modeling and dependency scanning into every phase of our project cycle.
Key Practices for ReactJS Security
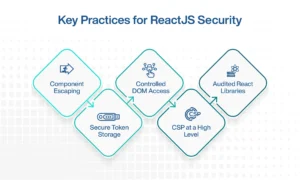
Securing your app doesn’t need a team of hackers; just smart tools and the right approach. Here’s how GKM IT protects React JS applications:
Component Escaping
React escapes content by default. GKM IT improves upon this with linting rules that raise warnings about unsafe rendering patterns and usage of dangerous attributes.
Secure Token Storage
Mitigating risk around token management, we leverage secure, HTTP-only cookies instead of localStorage or sessionStorage – in accordance with OWASP best practices.
Controlled DOM Access
We only access the DOM when absolutely necessary. Our React team wraps legacy integrations in isolated components to keep the rest of the application secure and unaffected.
CSP at a High Level
To protect against the execution of inline scripts, we apply strict CSP headers via middleware and proxies.
Audited React Libraries
We maintain a minimum set of trusted React libraries, routinely run automated scans for CVE entries, and review backwards compatibility while applying patches.
GKM IT’s DevSecOps Approach to ReactJS Development
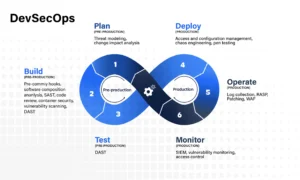
Security is not a checkbox; it’s a workflow. At GKM IT, we integrate security throughout the development lifecycle. Here’s a brief overview of the workflow:
1. Securing CI/CD Pipelines
We utilize services such as Snyk and Dependabot to find vulnerabilities in real time. Every build runs tests against a library of known React security vulnerabilities.
2. Security Code Reviews
Senior engineers who have been trained in ReactJS Security patterns review every pull request to help reduce risk at the code level.
3. Zero Trust to Third Parties
If you’re using analytics or third-party embeds, we sandbox them and enforce scoped permissions in order to protect your React components from bad actors.
When clients are working with GKM IT, they are not getting only an app, but a fortress in a front-end costume.
Designing React Applications with Secure Architecture
React is not just a library; it is a system. Here is how we build ReactJS applications for security and maintainability:
- Component Isolation: Distinct critical UI paths from user-generated content.
- SSO & Token Rotation: Secure sessions with refresh token patterns.
- SSR with Validation: Secure Server-Side Rendering with robust props validation and sanitization process.
- Scoped Global State: Reduce the potential of any global app state leakage, which limits exposure of data.
At GKM IT, security starts with your wireframes and is part of every deploy. From micro-frontends to monolithic dashboards, we will balance design with trust.
Conclusion: Secure by Design, Agile by Default
The future of front-end development is being dictated by the union of ReactJS development and security advancements. Our tooling and engineering-focused principles must also evolve as threat actors become more and more sophisticated.
ReactJS Security is not about being paranoid and worrying about everything that can possibly go wrong. It is about preparing for anything and everything going wrong while still delivering solid customer UX without leaving an open door for an attacker.
And if you’re seeking a partner who understands that duality, GKM IT is the one to help you lead the way. With us, you won’t just build nice React applications, you’ll build applications that withstand the test of scale, scrutiny, and time. Don’t let security be an afterthought. Choose GKM IT as your strategic partner to build high-quality, secure, and scalable ReactJS applications.
Related Blogs:
Capture and Share Screenshots in React Native
Reasons to choose React-Native for the future of your mobile app development
Frequently Asked Questions
1. What are common ReactJS security vulnerabilities?
XSS (JavaScript injection) and XSS attacks (unsafe DOM manipulation), insecure token storage, vulnerable libraries in ReactJS, etc., are all typical vulnerabilities. GKM IT addresses these threats by developing secure-by-design ReactJS and by implementing audits on dependencies.
2. How does React help prevent XSS?
ReactJS automatically escapes JSX output when rendering content, reducing the risks of XSS. At GKM IT, we take it a step further by sanitizing input data at runtime, adding Content Security Policy headers, and following best coding practices in every React application.
3. What security risks arise from direct DOM manipulation in ReactJS?
Bypassing React’s virtual DOM defences by gaining direct access to the DOM allows for more easily enabling XSS or injection attacks. GKM IT achieves this isolation with logic and follows a good structure in proper ReactJS development.
4. What best practices protect ReactJS applications?
Output encoding, secure token handling, prop validation, auditing React libraries, and safe use of CSP, etc., are key practices used by GKM IT and are applied to every secure and scalable ReactJS app they build.
5. How should a React app's security be tested?
Employ overlay testing, static analysis, and dependency scanning. GKM IT relies on embedded automated tests within CI/CD pipelines to catch any React security issues at the speed of development cycles, which will make your deployments safe and enterprise-level.